Tech tutorials Microsoft Sentinel: What Is It And How Can It Empower Security Operations Centres?
Microsoft Sentinel is a cloud-based SIEM and SOAR solution that automates response to security events, empowering security analysts to detect and respond to cyber threats.
By Insight Editor / 9 Feb 2024 / Topics: Artificial Intelligence (AI) , Cybersecurity
While traditionally, corporate security could get away with predefined prevention and detection mechanisms based on prior knowledge of attack methods, today, separating the wheat from the chaff is difficult. We often observe that admins frequently find themselves handling enormous volumes of events. And, more often than not, data quality is an issue, with false positives frequently leading to triage fatigue.
With the modern era of digitalisation, we now live in an identity-driven security perimeter. Today’s security teams face numerous challenges, including speed and sophistication of threats, and exponential growth of endpoints/assets and associated logs. Corporate security teams are drowning in the volumes of data being generated by digital assets. Data volumes are increasing every day as more operations are digitised and being able to triage quickly is important. The time window to respond when under attack is short; advanced adversaries typically only need hours to gain access, elevate privileges and exfiltrate data.
What is Microsoft Sentinel?
Microsoft Sentinel is a cloud-native Security Information and Event Management (SIEM) and Security Orchestration, Automation and Response (SOAR) solution built to provide security analysts with a powerful tool to detect and respond to cyberattacks. Sentinel’s SOAR capability is fully customisable and allows security teams to write playbooks that can (if desired) automate the entire response to a security event. For example, once Microsoft Sentinel identifies a malicious domain, a playbook that would automatically add a block rule to the company’s firewalls for that domain can be triggered.
Challenges of traditional Security Operations Centres (SOC)
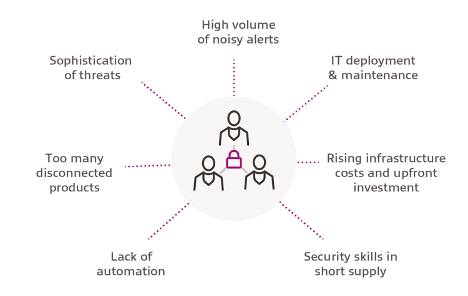
For the past decade, SOC leaders have tried to leverage SIEM technologies to establish a “single pane of glass” for their security operations. A “single pane of glass” means leveraging SIEM to identify and investigate security issues, which signifies that large volumes of data need to be ingested, processed, correlated and stored. Unfortunately, challenges with early SIEM technologies made this single-pane-of-glass view difficult because of the constant need to buy and install more hardware to handle increasing data volumes. SOC leaders faced a variety of challenges, including the following:
- Often, security teams were required to forego connecting data sources because of the costs associated with scaling out their SIEMs.
- Early search and correlation engines could not handle the volume of data, and analysts’ queries would time out before they completed their tasks.
- Static correlation rules often missed anomalies that (when combined with other contextual data) indicated that an attacker had successfully infiltrated a system.
- Typically, early SIEMs were not built with machine learning models to help identify such anomalies.
- Most corporate security teams cannot afford to hire their own data scientists to build, test and deploy their own models.
- Finally, many SIEM deployments were done with a “deploy and forget” mentality. This resulted in analysts working on a high number of false positives that strained personnel and made identifying the true, high-value events difficult. To be effective, SIEMs and their associated log providers require constant attention and fine-tuning.
How does Microsoft Sentinel helps with traditional SOC challenges?
Microsoft Sentinel is Microsoft’s cloud-native SIEM and SOAR solution. It is the first SIEM solution built into a major public cloud platform to help empower the security operations centres teams by leveraging cloud-native capabilities and addressing the traditional SIEM SecOps challenges by:
- Automatically scaling to meet the data collection and storage requirements for enterprises of any size
- Integrating directly with the Microsoft Intelligent Security Graph to help increase the likelihood of detecting advanced threats by leveraging Microsoft’s and its partners’ threat intelligence
- Including advanced anomaly detections using Microsoft’s machine learning algorithms, thus removing the need for companies to hire their own data scientists
- Reducing the need for human intervention by leveraging an open and flexible automation capability for investigating and responding to alerts
- Providing dashboards and user interfaces that are intuitive to analysts and built to streamline the typical operations within an SOC
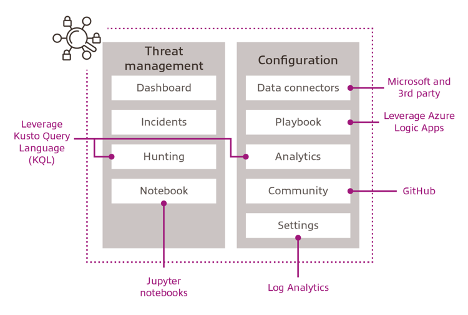
Microsoft Sentinel architecture
Microsoft Sentinel delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for alert detection, threat visibility, proactive hunting and threat response. Sentinel natively incorporates proven foundation services from Azure, such as Log Analytics and Logic Apps. Also, it enriches investigation and detection with Artificial Intelligence (AI) in conjunction with Microsoft's threat intelligence stream. The below diagram depicts major Microsoft Sentinel components.
What are the features of Microsoft Sentinel?
- Dashboards: Built-in dashboards provide data visualisation for connected data sources, which enables security analysts to deep dive into the events generated by those services.
- Incidents: An incident is an aggregation of all the relevant evidence for a specific investigation. It can contain one or multiple alerts, which are based on the analytics that you define.
- Hunting: This is a powerful tool for investigators and security analysts who need to proactively look for security threats. The searching capability is powered by Kusto Query Language (KQL).
- Notebooks: By integrating with Jupyter notebooks, Microsoft Sentinel extends the scope of what security analysts can do with the data that was collected. The notebooks feature combines full programmability with a collection of libraries for machine learning, visualisation and data analysis.
- Data connectors: Built-in connectors are available to facilitate data ingestion from Microsoft and partner solutions.
- Playbooks: A playbook is a collection of procedures that can be automatically executed upon an alert triggered by Microsoft Sentinel. Playbooks leverage Azure Logic Apps, which helps you automate and orchestrate tasks/workflows.
- Analytics: Analytics enable you to create custom alerts using Kusto Query Language (KQL).
- Community: The Microsoft Sentinel Community page is located on GitHub, and it contains detections based on different types of data sources that you can leverage in order to create alerts and respond to threats in your environment. The Microsoft Sentinel Community page also contains hunting query samples, playbooks, and other artifacts.
- Settings: Essentially, a Log Analytics workspace is a container that includes data and configuration information. Microsoft Sentinel uses this container to store the data that you collect from the different sources.
What is threat hunting in cybersecurity?
Threat hunting is the process of iteratively searching through a variety of data with the objective to identify threats in the systems. Threat hunting involves creating hypotheses about the attackers’ behavior and researching the hypotheses and techniques that were used to determine the artifacts that were left behind. As you can see in the figure below, Tier 3 is responsible for performing proactive hunting and advanced forensics. The goal of this team is to perform an analysis to identify anomalies that may indicate advanced adversaries. While most incidents are remediated at Tiers 1 and 2, only unprecedented findings or deviations from the norm are escalated to Tier 3 teams.
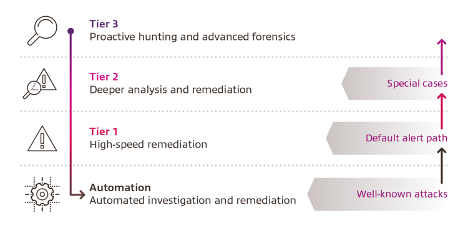
Microsoft Sentinel has a dedicated threat hunting capability designed specifically for hunt teams and Tier 3 analysts and ships with built-in hunting queries that have been written and tested by Microsoft security researchers and engineers. Within Sentinel, an analyst can create a new query, modify existing queries, bookmark, annotate, and tag interesting findings and launch a more detailed investigation.










